Constructive approach and randomization of a two-parameter chaos system for securing data
Keywords:
Two-parameter chaos system, Cryptosystems, Encryption algorithm, Lipschitz map, Pseudo-contractive operatorAbstract
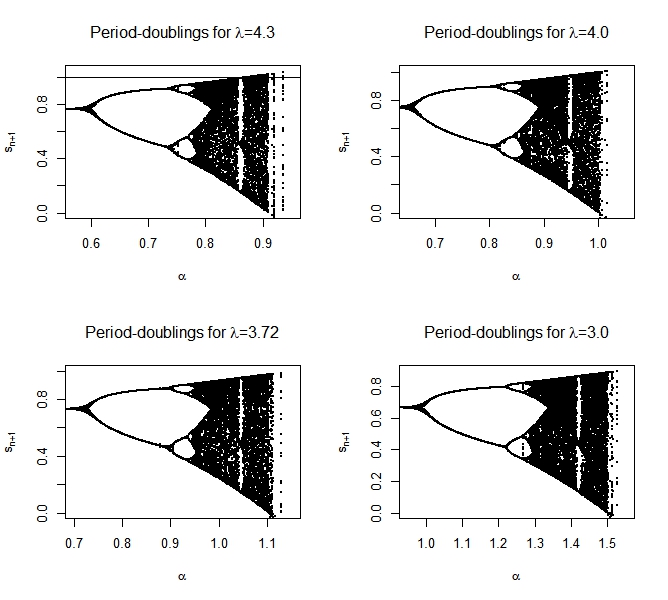
Secure communication techniques are important due to the increase in the number of technology users across the world. Likewise, a more random encryption algorithm suitable to secure data from unauthorised users is highly expected. This paper proposes a two-parameter nonlinear chaos map that is sensitive to the trio seed (s0, \alpha, \lambda) and has better information encryption. We introduce the parameter \alpha to linearise the conventional chaos system, which in turn brings a delay in the cryptosystems. The delay is a phenomenon that changes the chaotic features of a system. A small delay in the system leads to more aperiodicity and the unpredictability of the chaotic attractions. We normalise the new chaos map and use the Lipschitz and pseudo-contractive operators to obtain its irregularity region in Hilbert spaces. We also analyse the chaos map in terms of trajectory, Lyapunov exponent, complexity, and information entropy. Results obtained show that the new chaos map has a wide chaotic range and better statistical properties. It also maintains low complexity due to its linearity and produces more key spaces than most existing chaotic maps.
Published
How to Cite
Issue
Section
Copyright (c) 2024 Olalekan Taofeek Wahab, Salaudeen Alaro Musa, AbdulAzeez Kayode Jimoh, Kazeem Adesina Dauda

This work is licensed under a Creative Commons Attribution 4.0 International License.







