Development of a machine learning based fileless malware filter system for cyber-security
Keywords:
Perturbated, Malware, Cyber-attack, FilterAbstract
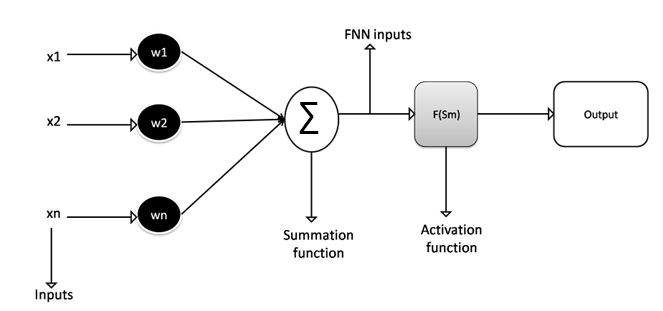
Over the years, the increased rate of perturbated malware based cyber-attack has presented many challenges and triggered the need for immediate solution all over the world. This was addressed in this paper development of a machine learning based fileless malware filter system for cyber security. Fileless malware which can come inform of Memory Resident Fileless malware or Windows Registry fileless malware are known to have no executable files, resides in the system memory or the windows registry. It doesn’t write any files to disk making it very challenging to detect us[1]ing traditional signature-based methods. It often leverage legitimate tools such as Windows Management Instrumentation and PowerShell to carry out its malicious activities. The methods used were data collection, data extraction, Deep Neural Network (DNN), activation function, training algorithm and classification. The methods were designed using structural and mathematical approaches which employed architectural diagrams, flow charts and self-defining equations to develop the new system. The training of the DNN was done using Gradient Descent Algorithms (GDA) to generate the malware filter algorithm. The filters were implemented with Simulink, tested and validated. The results were also evaluated using Regression (R) and Mean Square Error (MSE analyzer) and it showed R values of 0.9931 and MSE performance also recorded 0.002088Mu. This implied that the filter developed was able to detect and remove malware on the network.
Published
How to Cite
Issue
Section
Copyright (c) 2024 Umaru C. Obini, Chukwu Jeremiah, Sylvester A. Igwe

This work is licensed under a Creative Commons Attribution 4.0 International License.
How to Cite
Similar Articles
- Amos Orenyi Bajeh, Mary Olayinka Olaoye, Fatima Enehezei Usman-Hamza, Ikeola Suhurat Olatinwo, Peter ogirima Sadiku, Abdulkadir Bolakale Sakariyah, An adaptive neuro-fuzzy inference system for multinomial malware classification , Journal of the Nigerian Society of Physical Sciences: Volume 7, Issue 1, February 2025
- A. E. Ibor, D. O. Egete, A. O. Otiko, D. U. Ashishie, Detecting network intrusions in cyber-physical systems using deep autoencoder-based dimensionality reduction approach anddeep neural networks , Journal of the Nigerian Society of Physical Sciences: Volume 7, Issue 3, August 2025
- Shehu Magawata Shagari, Danlami Gabi, Nasiru Muhammad Dankolo, Noah Ndakotsu Gana, Countermeasure to Structured Query Language Injection Attack for Web Applications using Hybrid Logistic Regression Technique , Journal of the Nigerian Society of Physical Sciences: Volume 4, Issue 4, November 2022
- Oluwaseun IGE, Keng Hoon Gan, Ensemble feature selection using weighted concatenated voting for text classification , Journal of the Nigerian Society of Physical Sciences: Volume 6, Issue 1, February 2024
- Wilson Nwankwo, Kingsley Ukhurebor, Investigating the Performance of Point to Multipoint Microwave Connectivity across Undulating Landscape during Rainfall , Journal of the Nigerian Society of Physical Sciences: Volume 1, Issue 3, August 2019
- P. O. Odion, M. N. Musa, S. U. Shuaibu, Age Prediction from Sclera Images using Deep Learning , Journal of the Nigerian Society of Physical Sciences: Volume 4, Issue 3, August 2022
- Olayiwola Babarinsa, Olalekan Ihinkalu, Veronica Cyril-Okeme, Hailiza Kamarulhaili, Arif Mandangan, Azfi Zaidi Mohammad Sofi, Akeem B. Disu, Application of hourglass matrix in Goldreich-Goldwasser-Halevi encryption scheme , Journal of the Nigerian Society of Physical Sciences: Volume 4, Issue 4, November 2022
- Gabriel James, Ifeoma Ohaeri, David Egete, John Odey, Samuel Oyong, Enefiok Etuk, Imeh Umoren, Ubong Etuk, Aloysius Akpanobong, Anietie Ekong, Saviour Inyang, Chikodili Orazulume, A fuzzy-optimized multi-level random forest (FOMRF) model for the classification of the impact of technostress , Journal of the Nigerian Society of Physical Sciences: Volume 7, Issue 3, August 2025
- S. A. Osikoya, E. O. Adeyefa, Jensen-based New Cryptographic Scheme , Journal of the Nigerian Society of Physical Sciences: Volume 4, Issue 1, February 2022
- Gabriel James, Ime Umoren, Anietie Ekong, Saviour Inyang, Oscar Aloysius, Analysis of support vector machine and random forest models for classification of the impact of technostress in covid and post-covid era , Journal of the Nigerian Society of Physical Sciences: Volume 6, Issue 3, August 2024
You may also start an advanced similarity search for this article.






