Detecting network intrusions in cyber-physical systems using deep autoencoder-based dimensionality reduction approach anddeep neural networks
Authors
-
A. E. Ibor
Department of Computer Science, University of Calabar, Calabar, Nigeriahttps://orcid.org/0000-0002-4083-454X
-
D. O. Egete
Department of Computer Science, University of Calabar, Calabar, Nigeria
-
A. O. Otiko
Department of Computer Science, University of Cross River State, Calabar, Nigeria
-
D. U. Ashishie
Department of Computer Science, University of Calabar, Calabar, Nigeria
Keywords:
Adversarial attacks, Deep autoencoder, Deep learning, Intrusion detection, Cyber-physical systemsAbstract
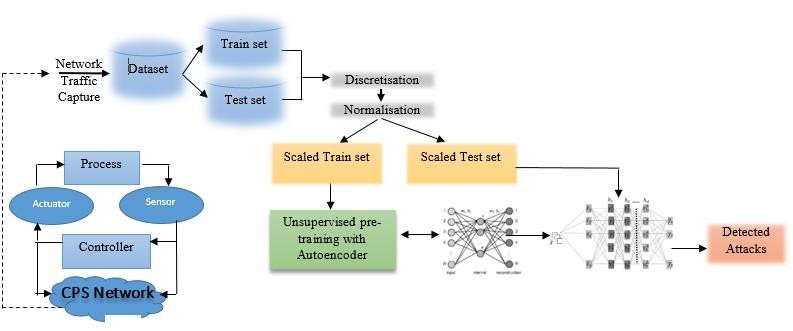
Cyber-Physical Systems (CPSs) that integrate computational and physical processes are the foundation of reliability in prominent areas of critical infrastructure, including transportation, energy, and manufacturing. The expansion in connected CPSs has made them vulnerable to various and changing intrusions into their networks. This research proposes a hybrid deep learning architecture that integrates the utilisation of a denoising autoencoder as a feature dimensionality reduction component with a five-layer deep feedforward neural network as an effective intrusion classifier. The model is trained and tested on CICIDS2017 and UNSW-NB15 datasets with a rich collection of attack patterns such as DoS, DDoS, Shellcode, and Worm attacks. The denoising autoencoder effectively learns higher-level representations of network traffic data, whereas the deep feedforward network facilitates precise multi-class classification. Empirical results demonstrate that the model achieves 99.99% and 99.95% detection accuracies on CICIDS2017 and UNSW-NB15 datasets, respectively, at very low false positive rates. Comparative analysis with state-of-the-art techniques further confirms the superior performance and generalisability of the presented solution, highlighting its applicability to real-time CPS threat detection systems.
Author Biography
A. E. Ibor
Senior Lecturer in Computer Science
Department of Computer Science
1] S. A. Ajagbe, J. B. Awotunde & H. Florez, “Ensuring intrusion detection for IoT services through an improved CNN”, SN Computer Science 5 (2023) 49. https://doi.org/10.1007/s42979-023-02448-y.
[2] J. B. Awotunde, Y. J. Oguns, K. A. Amuda, N. Nigar, T. A. Adeleke, K. M. Olagunju & S. A. Ajagbe, “Cyber-physical systems security: analysis, opportunities, challenges, and future prospects”, in Blockchain for Cyber-security in CyberPhysical Systems, pp. 21–46, 2023. https://link.springer.com/chapter/10.1007/978-3-031-25506-9 2.
[3] R. Alguliyev, Y. Imamverdiyev & L. Sukhostat, “Cyber-physical systems and their security issues”, Computers in Industry 100 (2018) 212. https://www.sciencedirect.com/science/article/abs/pii/S0166361517304244?via%3Dihub.
[4] A. O. de S´a, L. F. R. da Costa Carmo & R. C. Machado, “Covert attacks in cyberphysical control systems”, IEEE Trans. Industrial Informatics 13 (2017) 1641. http://dx.doi.org/10.1109/TII.2017.2676005.
[5] A. Hoehn and P. Zhang, Detection of covert attacks and zero dynamics attacks in cyberphysical systems, Proc. 2016 American Control Conf. (ACC), 2016 pp. 302–307. https://doi.org/10.1109/ACC.2016.7524819.
[6] A. Humayed, J. Lin, F. Li & B. Luo, “Cyberphysical systems security–A survey”, IEEE Internet Things J. 4 (2017) 1802. https://doi.org/10.1109/JIOT.2017.2703172.
[7] S. Ntalampiras, “Automatic identification of integrity attacks in cyber-physical systems”, Expert Systems with Applications, 58 (2016) 164. https://doi.org/10.1016/j.eswa.2016.04.006.
[8] F. Pasqualetti, F. D¨orfler & F. Bullo, “Attack detection and identification in cyberphysical systems”, IEEE Trans. Automatic Control 58 (2013) 2715. https://doi.org/10.1109/TAC.2013.2266831.
[9] A. O. Bajeh, M. O. Olaoye, F. E. UsmanHamza, I. S. Olatinwo, P. Ogirima, Sadiku & A. B. Sakariyah, “An adaptive neuro-fuzzy inference system for multinomial malware classification”, J. Nigerian Soc. Phys. Sci. 6 (2025) 2172. https://doi.org/10.46481/jnsps.2025.2172.
[10] H. A. Kholidy and A. Erradi, “VHDRA: a vertical and horizontal intelligent dataset reduction approach for cyber-physical power aware intrusion detection systems”, Security and Communication Networks (2019) 1283081. https://doi.org/10.1155/2019/6816943.
[11] G. Bernieri, E. Miciolino, F. Pascucci & R. Setola, “Monitoring system reaction in cyber-physical testbed under cyber-attacks”, Computers & Electrical Engineering 59 (2017) 86. https://doi.org/10.1016/j.compeleceng.2017.02.010.
[12] J. Wurm, Y. Jin, Y. Liu, S. Hu, K. Heffner, F. Rahman & M. Tehranipoor, “Introduction to cyber-physical system security: a cross-layer perspective”, IEEE Trans. Multi-Scale Computing Systems 3 (2016) 215. https://doi.org/10.1109/TMSCS.2016.2569446.
[13] A. G. Busygin, A. S. Konoplev & D. P. Zegzhda, “Providing stable operation of self-organizing cyber-physical system via adaptive topology management methods using blockchain-like directed acyclic graph”, Automatic Control and Computer Sciences 52 (2018) 1080. https://doi.org/10.3103/S0146411618080059.
[14] F. Nizam, S. Chaki, S. Al Mamun & M. S. Kaiser, Attack detection and prevention in the cyber physical system, in Proc. 2016 Int. Conf. Computer Communication and Informatics (ICCCI), Jan. 2016, pp. 1–6. https://doi.org/10.1109/ICCCI.2016.7480022.
[15] A. Y. Nur and M. E. Tozal, Defending cyber-physical systems against DoS attacks, in Proc. 2016 IEEE Int. Conf. Smart Computing (SMART-COMP), May 2016, pp. 1–3. https://doi.org/10.1109/SMARTCOMP.2016.7501685.
[16] C. Zimmer, B. Bhat, F. Mueller & S. Mohan,Time-based intrusion detection in cyber-physical systems, in Proc. 1st ACM/IEEE Int. Conf. Cyber-Physical Systems, Apr. 2010, pp. 109–118. https://doi.org/10.1145/1795194.179521.
[17] S. Karnouskos, Stuxnet worm impact on industrial cyber-physical system securit, in Proc. IECON 2011 - 37th Annu. Conf. IEEE Ind. Electronics Society, Nov. 2011, pp. 4490–4494. https://doi.org/10.1109/IECON.2011.6120048.
[18] P. Kreimel, O. Eigner & P. Tavolato, Anomaly-based detection and classification of attacks in cyber-physical systems, in Proc. 12th Int. Conf. Availability, Reliability and Security (ARES), Aug. 2017, pp. 1–6. https://doi.org/10.1145/3098954.3103155.
[19] C. Cheh, K. Keefe, B. Feddersen, B. Chen, W. G. Temple & W. H. Sanders,Developing models for physical attacks in cyber-physical systems, in Proc. 2017 Workshop on Cyber-Physical Systems Security and Privacy, Nov. 2017, pp. 49–55. https://doi.org/10.1145/3140241.3140249.
[20] A. Khaled, S. Ouchani, Z. Tari & K. Drira, “Assessing the severity of smart attacks in industrial cyber-physical systems”, ACM Transactions on Cyber-Physical Systems, 5 (2020) 1. https://doi.org/10.1145/3422369.
[21] L. S. L¨u, X. Jin, L. Ding & Q. Tan, “Adaptive sliding-mode control of a class of disturbed cyber–physical systems against actuator attacks”, Computers & Electrical Engineering 96 (2021) 107492. https://doi.org/10.1016/j.compeleceng.2021.107492.
[22] X. Fang, M. Xu, S. Xu & P. Zhao, “A deep learning framework for predicting cyber attacks rates”, EURASIP Journal on Information Security 2019 (2019) 11. https://doi.org/10.1186/s13635-019-0090-6.
[23] A. E. Ibor, F. A. Oladeji, O. B. Okunoye & O. O. Ekabua, “An improved cyberattack prediction technique with intelligent clustering and deep neural network”, FUW Trends in Science and Technology Journal 5 (2020) 15. http://www.ftstjournal.com/Digital%20Library/51%20Article%203.php.
[24] A. E. Ibor, F. A. Oladeji, O. B. Okunoye & O. O. Ekabua, “Conceptualisation of cyberattack prediction with deep learning”, Cybersecurity 3 (2020) 14. https://doi.org/10.1186/s42400-020-00053-7.
[25] A. Ibor, F. Oladeji, O. Okunoye & K. Abdulsalam, Network intrusion prediction model based on bio-inspired hyperparameter search, in Proc. nt. Conf. Electrical, Computer and Energy Technologies (ICECET), pp. 1–5, Dec. 2021. https://ieeexplore.ieee.org/abstract/document/9698491/.
[26] U. C. Obini, C. Jeremiah & S. A. Igwe, “Development of a machine learning based fileless malware filter system for cybersecurity”, J. Nigerian Soc. Phys. Sci. 5 (2024) 2192. https://doi.org/10.46481/jnsps.2024.2192.
[27] P. U. Emmoh & T. Moses, “A feature selection and scoring scheme for dimensionality reduction in a machine learning task”, J. Nigerian Soc. Phys. Sci. 6 (2025) 2273. https://doi.org/10.46481/jnsps.2025.2273.
[28] T. Tabassum, O. Toker & M. R. Khalghani, “Cyber–physical anomaly detection for inverter-based microgrid using autoencoder neural network”, Applied Energy, vol. 355, 122283, 2024. https://doi.org/10.1016/j.apenergy.2023.122283.
[29] N. O. Aljehane, “A secure intrusion detection system in cyberphysical systems using a parameter-tuned deep-stacked autoencoder”, Computers, Materials & Continua 68 (2021) 3915. https://doi.org/10.32604/cmc.2021.017905.
[30] Q. E. U. Haq, M. Imran, K. Saleem, T. Zia & J. Al Muhtadi, “Review on variants of restricted Boltzmann machines and autoencoders for cyber-physical systems”, in Internet of Things Security and Privacy, CRC Press, 2023, pp. 188–207. https://doi.org/10.1201/9781003199410.
[31] N. Rajathi, G. Saritha & V. J. Ramya, Adaptive intrusion detection in cyberphysical systems using reinforcement learning-based autoencoders, Proc. Int. Conf. Integrated Intelligence and Communication Systems (ICI-ICS), Nov. 2024, pp. 1–7. https://ieeexplore.ieee.org/abstract/document/10859561.
[32] D. Kaur, A. Anwar, I. Kamwa, S. Islam, S. M. Muyeen & N. Hossein-zadeh, “A Bayesian deep learning approach with convolutional feature engineering to discriminate cyber-physical intrusions in smart grid systems”, IEEE Access 11 (2023) 18910. https://doi.org/10.1109/ACCESS.2023.3247947.
[33] R. R. Nuiaa Al Ogaili, M. I. Mahdi, A. F. Neamah, S. A. A. Alradha Alsaidi, A. H. Alsaeedi, Z. A. Dashoor & S. Manickam, “PhishNetVAE cybersecurity approach: an integrated variational autoencoder and deep neural network approach for enhancing cybersecurity strategies by detecting phishing attacks”, Int. J. Intelligent Engineering & Systems 18 (2025) 123. .
[34] N. Sugunaraj & P. Ranganathan, Applications for autoencoders in power systems, in Proc. North American Power Symposium (NAPS), Oct. 2024, pp. 1–7. https://ieeexplore.ieee.org/abstract/document/10741685.
[35] A. Kousar, S. Ahmed, A. Altamimi, S. M. Kim & Z. A. Khan, Deep learning-based dimensionality reduction for anomaly detection in smart grids, in Proc. Int. Conf. Information and Communication Technology Convergence (ICTC), Oct. 2023, pp. 71–75. https://doi.org/10.1109/ICTC58733.2023.10393285.
[36] F. W. Alsaade & M. H. Al-Adhaileh, “Cyber attack detection for self-driving vehicle networks using deep autoencoder algorithms”, Sensors 23 (2023) 4086. https://doi.org/10.3390/s23084086.
[37] I. Ortega-Fernandez, M. Sestelo, J. C. Burguillo & C. Pi˜n´on-Blanco, “Network intrusion detection system for DDoS attacks in ICS using deep autoencoders”, Wireless Networks 30 (2024) 5059. https://doi.org/10.1007/s11276-022-03214-3.
[38] V. K. Kukkala, S. V. Thiruloga & S. Pasricha, “Real-time intrusion detection in automotive cyber-physical systems with recurrent autoencoders”, in Machine Learning and Optimization Techniques for Automotive Cyber-Physical Systems, Springer International Publishing, Cham, 2023, pp. 317–347. https://doi.org/10.1007/978-3-031-28016-0 10.
[39] K. Saranya & A. Valarmathi, “A multilayer deep autoencoder approach for cross layer IoT attack detection using deep learning algorithms”, Scientific Reports 15 (2025) 10246. https://doi.org/10.1038/s41598-025-93473-9.
[40] F. Harrou, B. Bouyeddou, A. Dairi & Y. Sun, “Exploiting autoencoder-based anomaly detection to enhance cybersecurity in power grids”, Future Internet 16 (2024) 184. https://doi.org/10.3390/fi16060184.
[41] J. Zhang, L. Pan, Q. L. Han, C. Chen, S. Wen & Y. Xiang, “Deep learning based attack detection for cyber-physical system cybersecurity: a survey”, IEEE/CAA Journal of Automatica Sinica 9 (2022) 377. https://doi.org/10.1109/JAS.2021.1004261.
[42] G. D’Angelo & F. Palmieri, “A stacked autoencoder-based convolutional and recurrent deep neural network for detecting cyberattacks in interconnected power control systems”, International Journal of Intelligent Systems 36 (2021) 7080. https://doi.org/10.1002/int.22581.
[43] M. J. Zideh, M. R. Khalghani & S. K. Solanki, “An unsupervised adversarial autoencoder for cyber attack detection in power distribution grids”, Electric Power Systems Research 232 (2024) 110407. https://ui.adsabs.harvard.edu/abs/2024EPSR..23210407Z/abstract.
[44] Z. Ma, G. Mei & F. Piccialli, “Deep Learning for Secure Communication in Cyber-Physical Systems”,IEEE Internet of Things Magazine 5 (2022) 63. Dhttps://ieeexplore.ieee.org/abstract/document/9889272.
[45] B. Roshanzadeh, J. Choi, A. Bidram & M. Mart´?nez-Ram´on, “Multivariate time-series cyberattack detection in the distributed secondary control of AC microgrids with convolutional neural network autoencoder ensemble”, Sustainable Energy, Grids and Networks 38 (2024) 101374. https://doi.org/10.1016/j.segan.2024.101374.
[46] M. Chen, X. Shi, Y. Zhang, D. Wu & M. Guizani, “Deep feature learning for medical image analysis with convolutional autoencoder neural network”, IEEE Transactions on Big Data 7 (2021) 750. https://doi.org/10.1109/TBDATA.2017.2717439.
[47] X. Jin, W. M. Haddad & T. Yucelen, “An adaptive control architecture for mitigating sensor and actuator attacks in cyber-physical systems”, IEEE Transactions on Automatic Control 62 (2017) 6058. https://doi.org/10.1109/TAC.2017.2652127.
[48] Md. Shamsul Huda, Md. Suruz Miah, Mohammad Mehedi Hassan, Md. Rafiqul Islam, John Yearwood, Majed A. Alrubaian & Ahmad Almogren, “Defending unknown attacks on cyber-physical systems by semisupervised approach and available unlabeled data”, Information Sciences 379 (2017) 211. https://doi.org/10.1016/j.ins.2016.09.041.
[49] O. A. Beg, T. T. Johnson & A. Davoudi, “Detection of false-data injection attacks in cyber-physical DC microgrids”, IEEE Transactions on Industrial Informatics 13 (2017) 2693. https://doi.org/10.1109/TII.2017.2656905.
[50] S. R. Chhetri, A. Canedo & M. A. Al Faruque, Kcad: kinetic cyber-attack detection method for cyber-physical additive manufacturing systems, in Proc. 35th Int. Conf. Computer-Aided Design (ICCAD), San Jose, CA, USA, Nov. 2016, pp. 1–8. https://doi.org/10.1145/2966986.2967050.
[51] H. Sadreazami, A. Mohammadi, A. Asif & K. N. Plataniotis, “Distributed-graph-based statistical approach for intrusion detection in cyber-physical systems”, IEEE Transactions on Signal and Information Processing over Networks 4 (2017) 137. https://doi.org/10.1109/TSIPN.2017.2749976.
[52] A. Ferdowsi & W. Saad, Generative adversarial networks for distributed intrusion detection in the internet of things, in Proc. 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, Dec. 2019, pp. 1–6. https://doi.org/10.1109/GLOBECOM38437.2019.9014102.
[53] Y. Hong, U. Hwang, J. Yoo & S. Yoon, “How generative adversarial networks and their variants work: an overview”, ACM Computing Surveys 52 (2019) 1. https://doi.org/10.1145/3301282.
[54] K. Wang, C. Gou, Y. Duan, Y. Lin, X. Zheng & F. Y. Wang, “Generative adversarial networks: introduction and outlook”, IEEE/CAA Journal of Automatica Sinica 4 (2017) 588. https://doi.org/10.1109/JAS.2017.7510583.
[55] S. Thakur, A. Chakraborty, R. De, N. Kumar & R. Sarkar, “Intrusion detection in cyberphysical systems using a generic and domain specific deep autoencoder model”, Computers & Electrical Engineering 91 (2021) 107044. https://doi.org/10.1016/j.compeleceng.2021.107044.
[56] I. Sharafaldin, A. Gharib, A. H. Lashkari & A. A. Ghorbani, “Towards a reliable intrusion detection benchmark dataset”, Software Networking 2018 (2018) 177. https://www.researchgate.net/publication/318286637_Towards_a_Reliable_Intrusion_Detection_Benchmark_Dataset.
[57] I. Sharafaldin, A. H. Lashkari & A. A. Ghorbani, Toward generating a new intrusion detection dataset and intrusion traffic characterization, in Proc. 4th Int. Conf. Information Systems Security and Privacy (ICISSP), Funchal, Madeira, Portugal, Jan. 2018, pp. 108–116. https://doi.org/10.5220/0006639801080116.
[58] I. Sharafaldin, A. Habibi Lashkari & A. A. Ghorbani, “A detailed analysis of the CICIDS2017 data set,” in Information Systems Security and Privacy, P. Mori, S. Furnell & O. Camp (Eds.), Communications in Computer and Information Science, vol. 977, Springer, Cham, 2019, pp. 172–188. https://doi.org/10.1007/978-3-030-25109-3 9.
[59] R. Panigrahi & S. Borah, “A detailed analysis of CICIDS2017 dataset for designing intrusion detection systems”, International Journal of Engineering and Technology 7 (2018) 479.
[60] T. Chadza, K. G. Kyriakopoulos & S. Lambotharan, Contemporary sequential network attacks prediction using hidden Markov model, Proc. 17th Int. Conf. Privacy, Security and Trust (PST), Montreal, Canada, July 2019, pp. 1–3. https://doi.org/10.1109/PST47121.2019.8949035.
[61] O. Faker & E. Dogdu, Intrusion detection using big data and deep learning techniques, Proc. ACM Southeast Conf., Huntsville, AL, USA, Apr. 2019, pp. 86–93. https://doi.org/10.1145/3299815.3314439.
[62] R. Vinayakumar, M. Alazab, K. P. Soman, P. Poornachandran, A. AlNemrat & S. Venkatraman, “Deep learning approach for intelligent intrusion detection system”, IEEE Access 7 (2019) 41525. https://doi.org/10.1109/ACCESS.2019.2895334.
[63] N. Moustafa & J. Slay, , “UNSW-NB15: a comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set)”, 2015 Military Commun. & Inf. Syst. Conf. (MilCIS), Canberra, Australia, Nov. 2015, pp. 1–6. https://doi.org/10.1109/MilCIS.2015.7348942.
[64] T. Janarthanan & S. Zargari, “Feature selection in UNSW-NB15 and KD-DCUP’99 datasets”, 2017 IEEE 26th Int. Symp. Industrial Electronics (ISIE), Edinburgh, UK, June 2017, pp. 1881–1886. https://doi.org/10.1109/ISIE.2017.8001537.
[65] N. Moustafa & J. Slay, “The evaluation of network anomaly detection systems: statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set”, Inf. Security J.: A Global Perspective 5 (2016) 18. https://doi.org/10.1080/19393555.2015.1125974.
[66] Q. Meng, D. Catchpoole, D. Skillicom & P. J. Kennedy, Relational autoencoder for feature extraction, Proc. 2017 Int. Joint Conf. Neural Networks (IJCNN), Anchorage, AK, USA, May 2017, pp. 364–371. https://doi.org/10.1109/IJCNN.2017.7965877.
[67] S. Li, J. Kawale & Y. Fu, Deep collaborative filtering via marginalized denoising auto-encoder, Proc. 24th ACM Int. Conf. Information and Knowledge Management (CIKM), Melbourne, Australia, Oct. 2015, pp. 811–820. https://doi.org/10.1145/2806416.2806527.
[68] C. Lu, Z. Y. Wang, W. L. Qin & J. Ma, “Fault diagnosis of rotary machinery components using a stacked denoising autoencoder-based health state identification”, Signal Process. 130 (2017) 377. https://doi.org/10.1016/j.sigpro.2016.07.028.
[69] X. Lu, Y. Tsao, S. Matsuda & C. Hori, “Speech enhancement based on deep denoising autoencoder”, in Interspeech, Lyon, France, Aug. 2013, pp. 436–440. https://cir.nii.ac.jp/crid/1360292619441675904.
[70] C. Xing, L. Ma & X. Yang, “Stacked denoise autoencoder based feature extraction and classification for hyperspectral images”, J. Sensors (2016) 2975718. http://dx.doi.org/10.1155/2016/3632943.
[71] C. C. Aggarwal, Neural networks and deep learning, Springer, Cham, 2018. https://doi.org/10.1007/978-3-031-29642-0.
[72] I. Goodfellow, Y. Bengio & A. Courville, Deep learning, MIT Press, Cambridge, MA, USA, 2016. https://doi.org/10.4258/hir.2016.22.4.351.
[73] D. Ding, Q. L. Han, Y. Xiang, X. Ge & X. M. Zhang, “A survey on security control and attack detection for industrial cyber-physical systems”, Neurocomputing 275 (2018) 1674. https://doi.org/10.1016/j. neucom.2017.10.009.
[74] J. Giraldo, D. Urbina, A. Cardenas, J. Valente, M. Faisal, J. Ruths, N. O. Tippenhauer, H. Sandberg & R. Candell, “A survey of physics-based attack detection in cyber-physical systems”, ACM Comput. Surveys 51 (2018) 1. https://doi.org/10.1145/3203245.
[75] S. Patro & K. K. Sahu, “Normalization: a preprocessing stage”, arXiv preprint arXiv:1503.06462, 2015. https://arxiv.org/abs/1503.06462.
[76] M. Chen, X. Shi, Y. Zhang, D. Wu & M. Guizani, “Deep feature learning for medical image analysis with convolutional autoencoder neural network”, IEEE Trans. Big Data 7 (2021) 750. https://doi.org/10.1109/TBDATA.2017.2717439.
[77] Y. Wang, H. Yao & S. Zhao, “Auto-encoder based dimensionality reduction”, Neurocomputing 184 (2016) 232. https://doi.org/10.1016/j.neucom.2015.08.104.
[78] W. Wang, Y. Huang, Y. Wang & L. Wang, Generalized autoencoder: a neural network framework for dimensionality reduction, in Proc. IEEE Conf. Computer Vision and Pattern Recognition Workshops, Columbus, OH, USA, June 2014, pp. 490–497. https://doi.org/10.1109/CVPRW.2014.79.
[79] M. Yousefi-Azar, V. Varadharajan, L. Hamey & U. Tupakula, “Autoencoder-based feature learning for cyber security applications”,2017 Int. Joint Conf. Neural Networks (IJCNN), Anchorage, AK, USA, May 2017, pp. 3854–3861. https://doi.org/10.1109/IJCNN.2017.7966342.
[80] A. F. Agarap, “Deep learning using rectified linear units (ReLU)”, arXiv preprint arXiv:1803.08375, 2018. https://arxiv.org/abs/1803.08375.
[81] M. Abadi, P. Barham, J. Chen, Z. Chen, A. Davis, J. Dean, M. Devin, S. Ghemawat, G. Irving, M. Isard, M. Kudlur, J. Levenberg, R. Monga, S. Moore, D. G. Murray, B. Steiner, P. Tucker, V. Vasudevan, P. Warden, M. Wicke, Y. Yu & X. Zheng, TensorFlow: A System for Large-Scale Machine Learning, 12th USENIX Symposium on Operating Systems Design and Implementation (OSDI 16), Savannah, GA, USA, Nov. 2–4, 2016, pp. 265–283. https://www.usenix.org/conference/osdi16/technical-sessions/presentation/abadi.
[82] B. Ramsundar & R. B. Zadeh, TensorFlow for Deep Learning: From Linear Regression to Reinforcement Learning, O’Reilly Media, Sebastopol, CA, USA, 2018. https://dl.acm.org/doi/abs/10.5555/3235300.
[83] Y. Wang, J. Liu, J. Miši?, V. B. Miši?, S. Lv & X. Chang, “Assessing optimizer impact on DNN model sensitivity to adversarial examples”, IEEE Access 7 (2019) 152766. https://doi.org/10.1109/ACCESS.2019.2948658.
[84] M. D. Zeiler, “ADADELTA: an adaptive learning rate method”, arXiv preprint arXiv:1212.5701, 2012. https://arxiv.org/abs/1212.5701.
[85] J. Hartford, G. Lewis, K. Leyton-Brown & M. Taddy, Deep IV: A Flexible Approach for Counterfactual Prediction, Proceedings of the 34th International Conference on Machine Learning, Sydney, NSW, Australia, Aug. 6–11, 2017, pp. 1414–1423. http://proceedings.mlr.press/v70/hartford17a.html.
Published
How to Cite
Issue
Section
Copyright (c) 2025 A. E. Ibor, D. O. Egete, A. O. Otiko, D. U. Ashishie

This work is licensed under a Creative Commons Attribution 4.0 International License.







