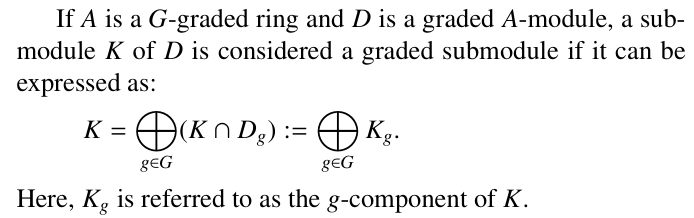Why Publish With JNSPS
We are committed to supporting you throughout your publishing “journey” – from submission, through peer review, to publication and promotion
Open Access
JNSPS is a strong supporter of open access (OA). All the research articles published in JNSPS are fully open access.
Read moreRefereed
Peer review process - Committed to serving the scientific community. JNSPS uses a single-blind peer-review process.
Read moreIndexed
The journal is indexed and abstracted in DOAJ, Crossref, Scopus, Google Scholar, WorldCat, Researchgate, etc.
Read more100,000 NGN
APC is 100,000 NGN as an active Nigerian member of NSPS. Non-member/non-active member of NSPS pays 300 USD or its Naira equivalence
Read moreCurrent Issue
It is with great pleasure that we present Volume 8, Issue 1 of the Journal of the Nigerian Society of Physical Sciences (JNSPS). This issue reflects the journal’s sustained commitment to publishing rigorous, interdisciplinary, and globally relevant research across Chemistry, Computer Science, Earth Sciences, Mathematics & Statistics, and Physics & Astronomy. The diversity and depth of contributions in this volume underscore the vibrancy of contemporary scientific inquiry and the growing international footprint of the journal.
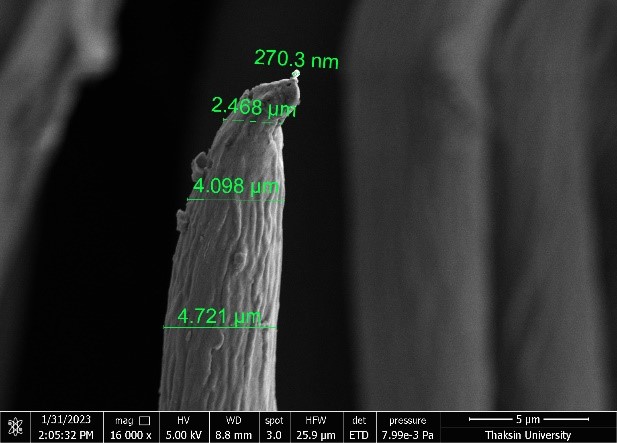
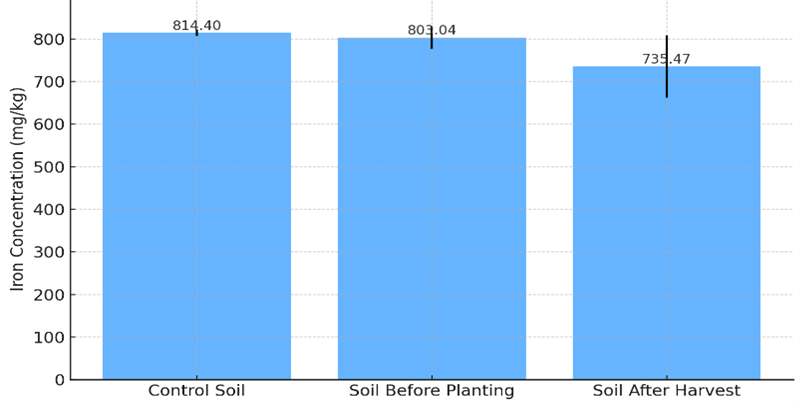
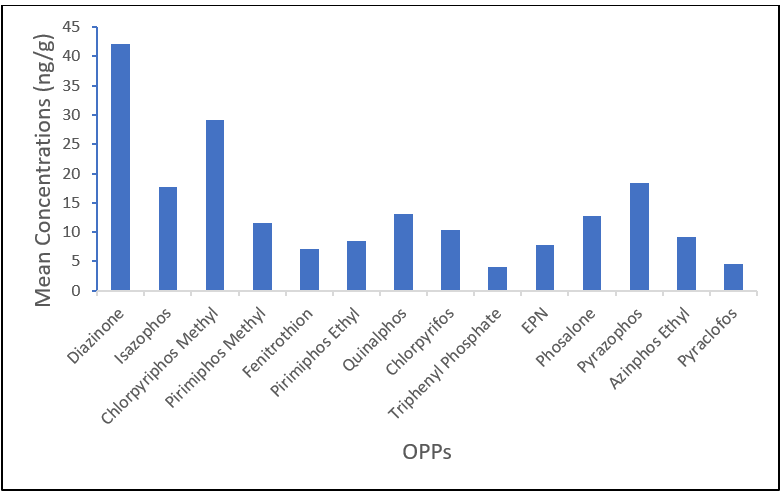
In Chemistry, this issue opens with a nanostructured materials study on the hydrophobicity of golden-phase leaves coated with zinc oxide-based nanocomposite, supported by highly magnified SEM analyses of hair-like surface morphologies. Complementing this materials-focused contribution are two environmentally significant investigations: a comprehensive risk assessment of cadmium, zinc, iron, and copper contamination in crops and soils at an Enugu dumpsite, and a detailed evaluation of organophosphate pesticide residues in spices and herbs sold in Southern Nigeria. Together, these studies address pressing concerns at the interface of materials science, environmental chemistry, and public health.
The Computer Science section highlights the transformative role of artificial intelligence and data-driven methodologies in socio-economic systems. A novel hybrid framework integrating K-means clustering, Naïve Bayes classification, and knowledge graphs advances precision agriculture through synergistic intelligence modeling. In parallel, a robust machine learning–based approach to credit default prediction in Uganda demonstrates the increasing relevance of computational analytics in financial risk management within emerging economies.
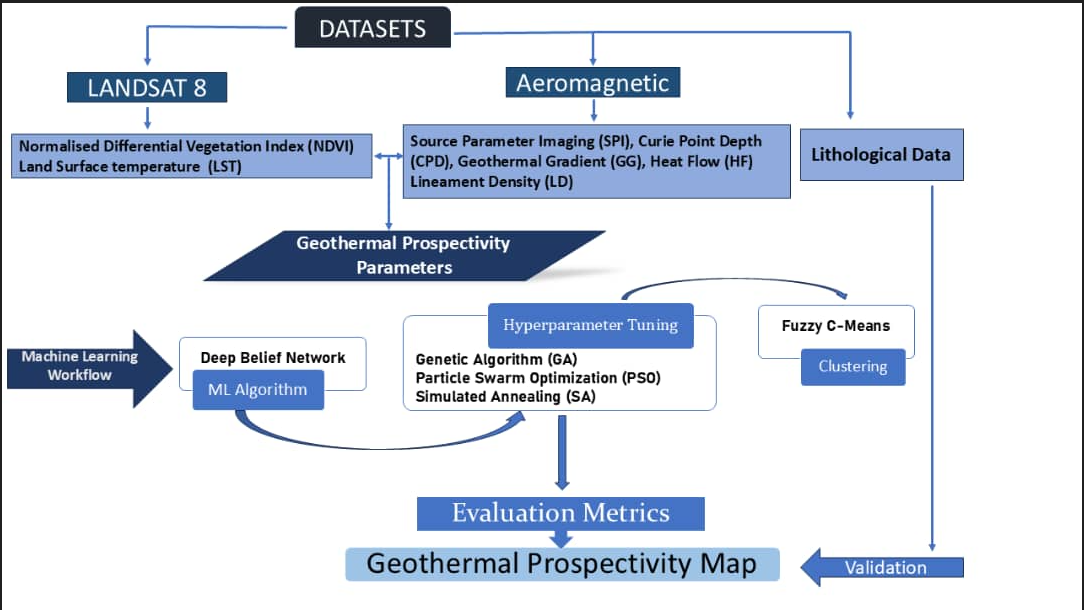
In Earth Sciences, the integration of geophysical data with advanced learning architectures is exemplified in a hybrid deep belief network and fuzzy clustering approach for geothermal prospectivity mapping in Northeastern Nigeria using magnetic and Landsat datasets. Additionally, a multi-proxy stratigraphic investigation of exposed formations in the Benin Flank provides refined nomenclature evidence for the Mamu Formation within the Anambra Basin. These contributions reinforce the importance of data fusion and sedimentological reconstruction in understanding subsurface resources and basin evolution.
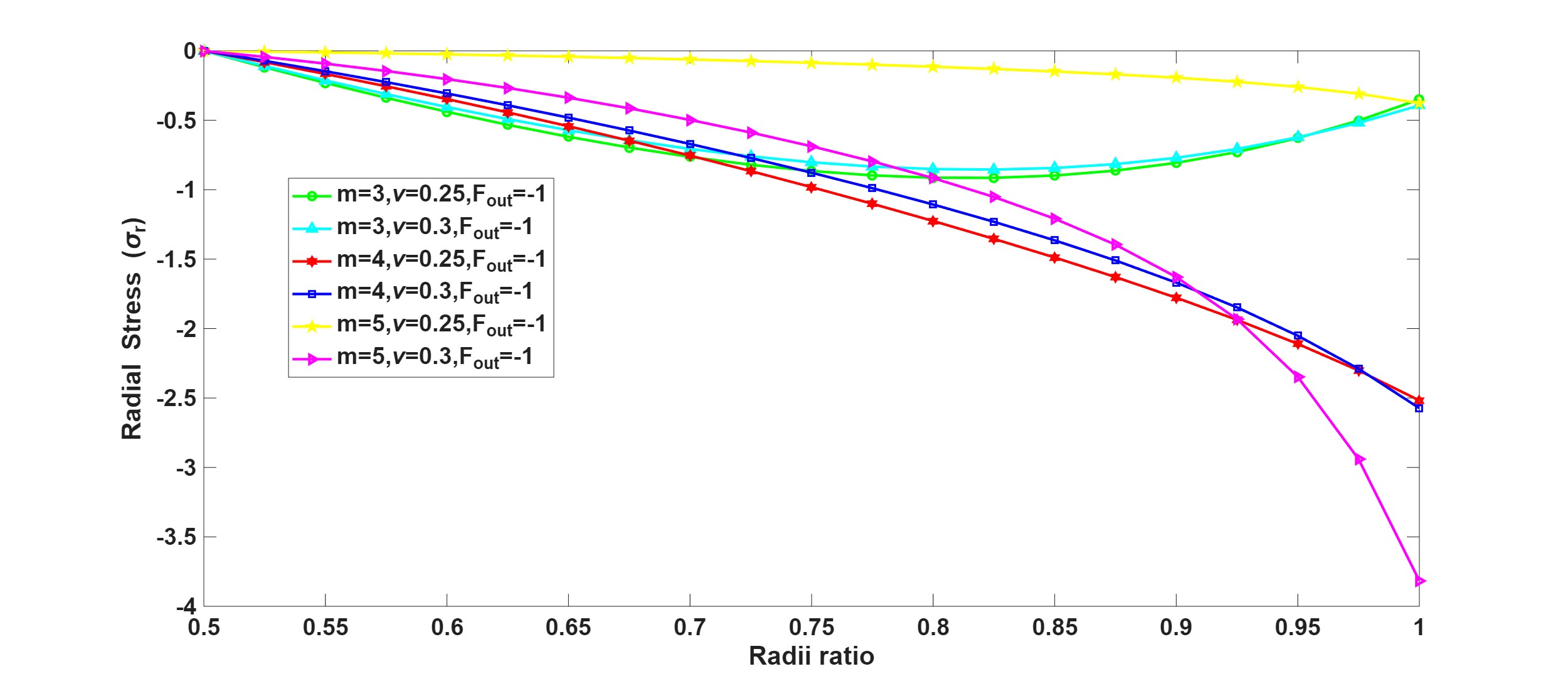
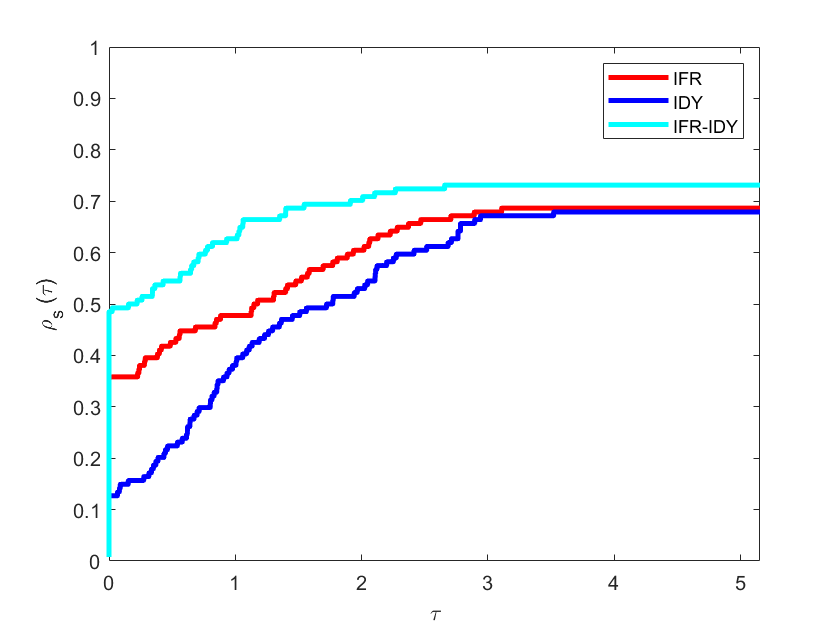
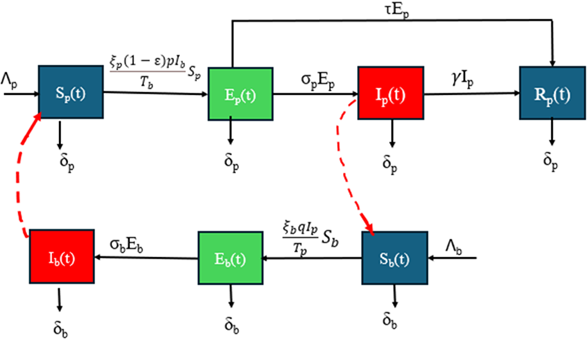
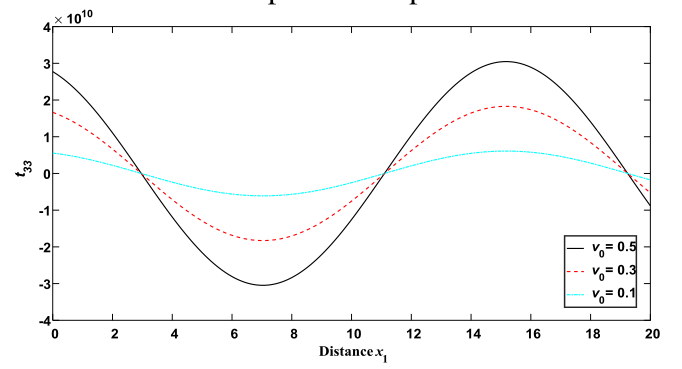
The Mathematics & Statistics section presents a rich spectrum of theoretical and applied analyses. From computational optimization of auctioneer revenue in modified discrete Dutch auctions under CARA risk preferences, to mechanical modeling of functionally graded discs with radial non-uniformity, the issue demonstrates the power of analytical modeling in economics and materials science. Further contributions include a hybrid IFR-IDY conjugate gradient algorithm for unconstrained optimization with portfolio applications, a Caputo–Fabrizio fractional model for onchocerciasis control emphasizing early treatment and vector management, structural investigations in graded module theory, and thermoelastic analysis of moving thermal loads in modified couple stress media. Collectively, these works highlight the centrality of mathematical abstraction in addressing engineering, epidemiological, and financial challenges.
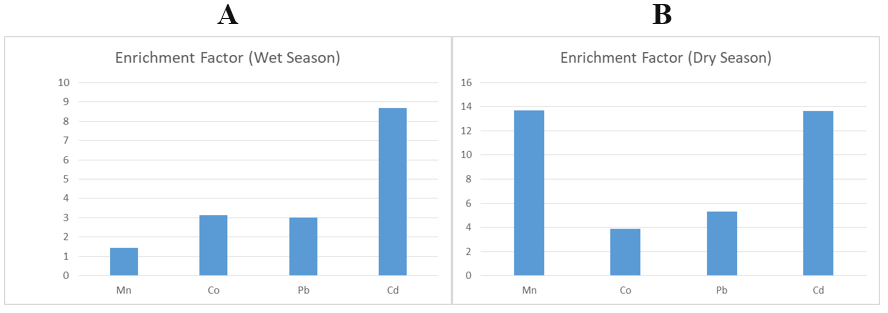
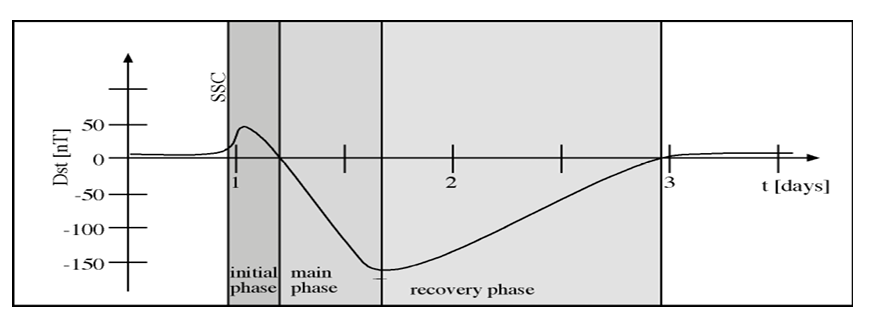
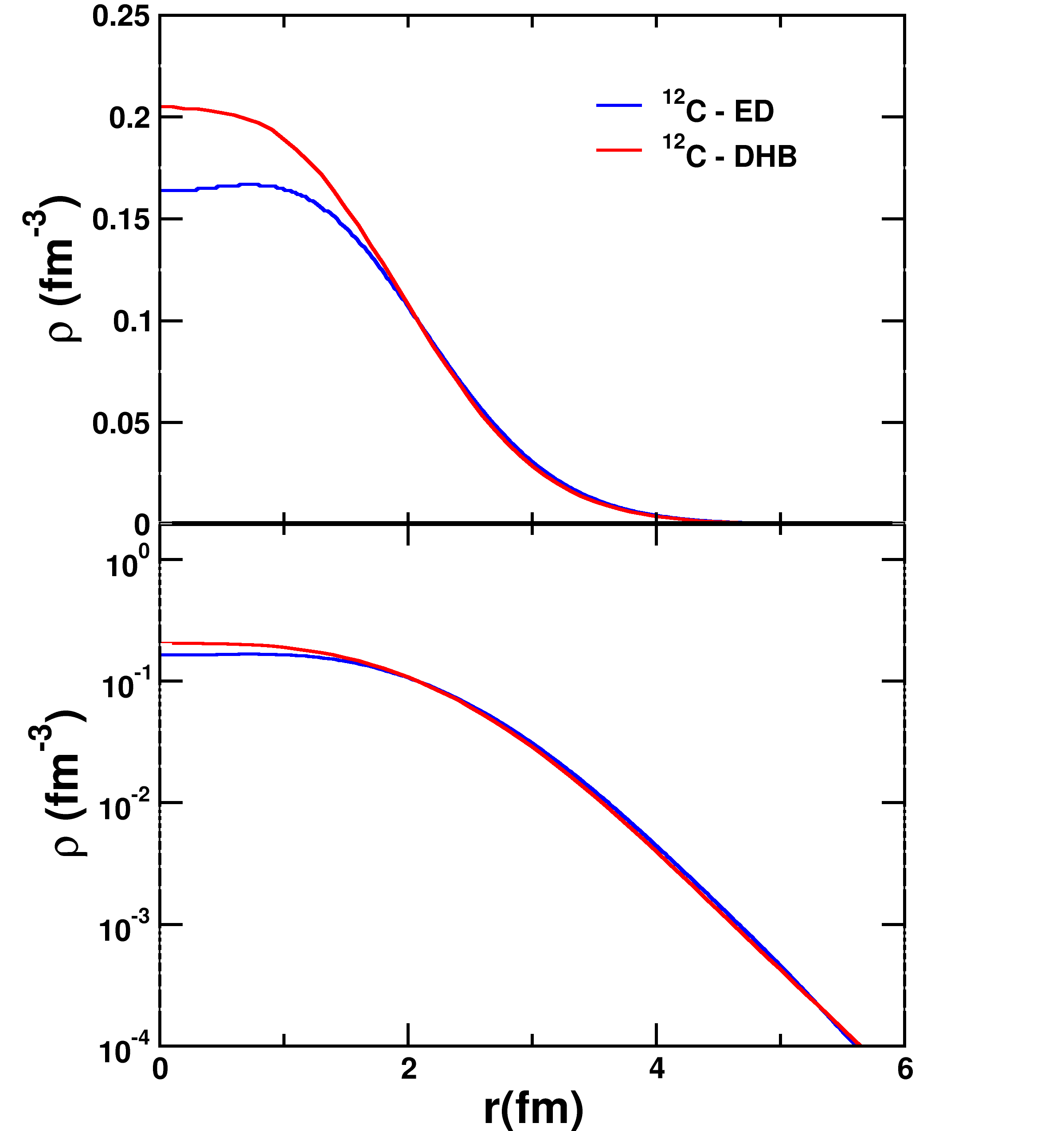
In Physics & Astronomy, this volume features both theoretical and experimental explorations. A velocity-in/dependent double-folding analysis of the 12C+12C^{12}\mathrm{C}+^{12}\mathrm{C}12C+12C elastic scattering cross-section deepens understanding of nuclear interaction potentials. Complementary studies examine radiation shielding properties of palm nut shell ash–modified concrete, first-principles calculations of structural and optical properties in ternary alloys, heavy metal concentrations in indoor dust with implications for pediatric exposure, comparative computation of vibrational partition functions via Poisson summation and classical limits, and magnetopause dynamics during Solar Cycle 24 in relation to CME-driven geomagnetic storms. These investigations collectively traverse scales—from subatomic interactions to planetary magnetospheric dynamics—illustrating the breadth of physical science research represented in this issue.
As JNSPS continues to consolidate its position within international indexing platforms, the editorial board remains committed to rigorous peer review, ethical publishing standards, and the promotion of high-impact scholarship. We express our sincere appreciation to our authors, reviewers, associate editors, and the broader scientific community whose dedication sustains the quality and integrity of the journal.
We invite readers to engage deeply with the contributions in this issue and to continue partnering with us in advancing scientific knowledge for national development and global relevance.
B. J. Falaye, PhD, LNSPS
Editor-in-Chief, Journal of the Nigerian Society of Physical Sciences (JNSPS)